Page 2 of 3
Encryption Technology - What Encryption Features / Requirements are Important?
There are many data encryption solutions available. When evaluating an encryption solution for the protection of sensitive data, it is important that key features and certifications are present to ensure compliance, resiliency, security and disaster recovery.
-
FIPS 140-2 Compliant Encryption
- Federal Information Process Standard (FIPS 140-2) is a U.S. government computer security standard used to accredit cryptographic modules. The title is “Security Requirements for Cryptographic Modules”.
- Federal agencies and departments validate that the module in use is covered by an existing FIPS 140-2 certificate. As an example, Alliance’s encryption implementation is covered by Security Certificate #1747 under the Consolidated Certificate No. 0018.
- The Cryptographic Module Validation Program (CMVP), a joint effort by the National Institute of Standards and Technology (NIST) and Communications Security Establishment Canada (CSEC) to ensure that encryption implementations adhere to the FIPS 140-2 standards.
-
AES-256 bit Encryption
- The Advanced Encryption Standard (AES) is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST). AES has been adopted by the U.S. government and is now used worldwide. With AES, NIST selected three members of the Rijndael family, with three different key lengths: 128, 192 and 256 bits.
- For data to be retained past the year 2031, AES-256 bit encryption is required. The 256-bit encryption requires the use of a 256-bit (32 characters) key, providing a stronger key more resistant to hacking via the use of supercomputers.
-
Encryption Modes
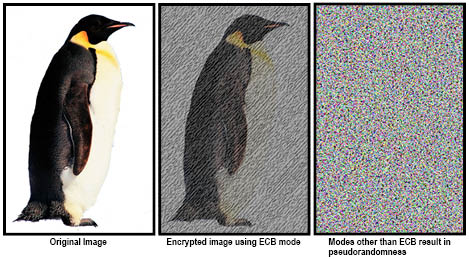
- When implementing the AES-256 bit encryption, different encryption modes can be utilized. To protect data it is important that modes be utilized that protect all types of data from access or interpretation. As an example, the illustration shows an image that is encrypted using both Electronic Code Book ECB and Cipher Block Chaining (CBC) modes.
- Alliance’s encryption implementation utilizes Cipher Block Chaining (CBC), to ensure that all data (such as images), are obscured from recognition or interpretation. Imagine in the above example if the subjects were classified satellite images, using ECB mode encryption would not protect disclosure of the data, hence making the encryption implementation ineffective.