Data Encryption Technology
In today’s environment, the protection of sensitive data is imperative. Government and corporate compliance mandates are stiffening. HIPAA HITECH regulations now call for significant fines when personal health information is exposed, as well as public notification of such breaches. To protect sensitive data, encryption is the most effective way to achieve security. If data cannot be viewed then no breach can occur.
What is Data encryption?
Data encryption is the process of transforming plain text data (native format), using encryption algorithms and secret encryption keys, to an encrypted format (cipher text). To then utilize the data one must know the secret encryption key required to transform the data from cipher text to plain text.
Data Encryption Technology - Types of Encryption Keys based Upon Need
There are many varied data encryption solutions in the market today. One must consider the purpose and use planned when determining the best approach to be selected.
-
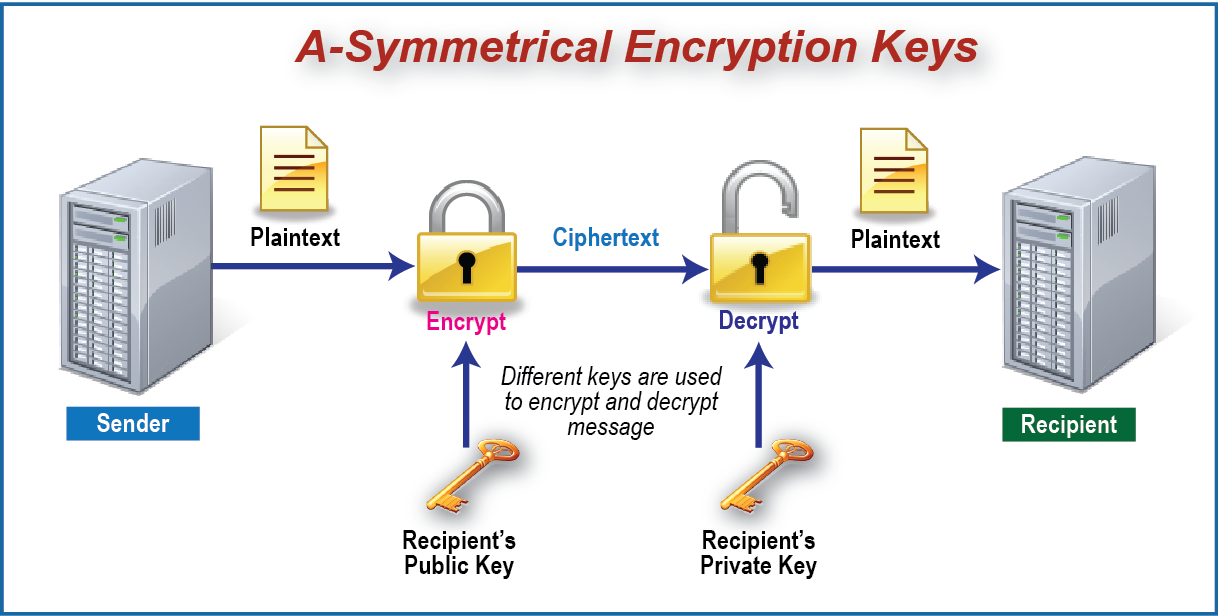
A-Symmetrical Encryption Keys:

- On the following diagram on the right, an A-Symmetrical Encryption Key is utilized.In this case, a key pair (consisting of a public key and a private key) is utilized to encrypt and then decrypt the data respectively. This approach is very useful for sending data over email to secure data access. Keys are shared with other recipients requiring access to the data.
-
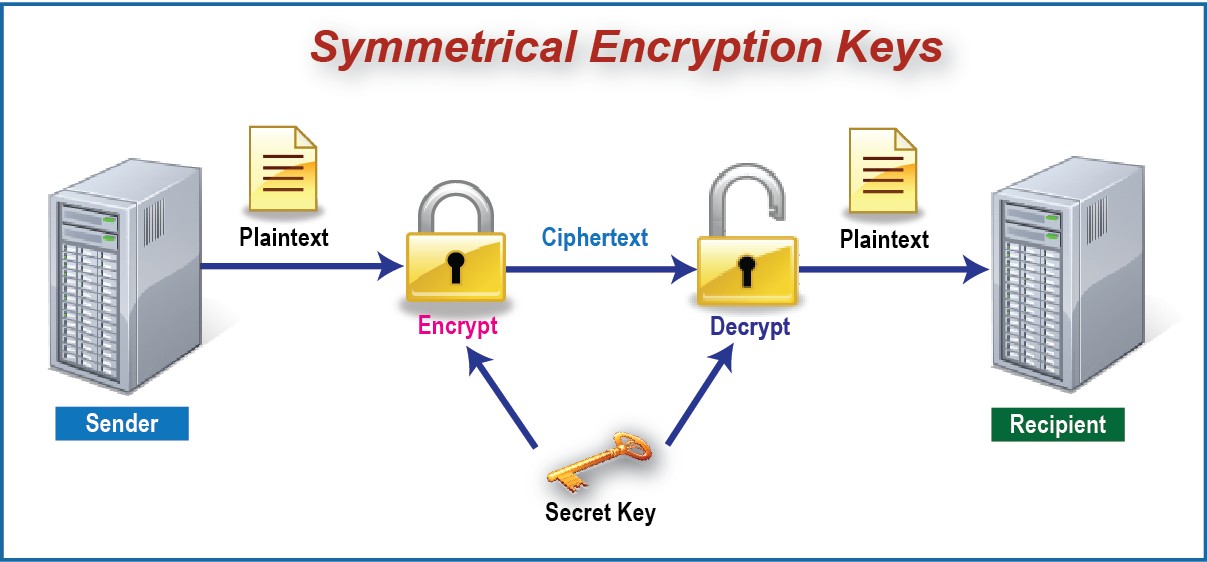
Symmetrical Encryption Keys:

- Depicted in the following diagram, a Symmetrical Encryption Key is utilized. In this case, the same unique key is utilized to encrypt and later decrypt data. This is very useful with storage devices eliminating the need to make a public key accessible to users that need to view the data. With centralized servers in an enterprise environment, where user authentication is guaranteed, this greatly simplifies access to secured data.